Turn Compliance into Action
We turn complex requirements into secure, audit-ready setups from day one.







From next-gen startups to established businesses













.avif)


IT Compliance, Handled
From encryption to access policies, we set the foundation so your company is IT compliant from day one.

Information Security & Access Control
From incident response to role-based access and device-level authentication. Your data stays secure and only the right people get in.


Malware Protection, Built In
Real-time scanning, endpoint security, and MDM policies help stop threats early. Alerts go straight to support — so action is fast, and recovery is always prepared.
System Security & Activity Tracking
Track hardware, software, and security events via MDM and SentinelOne (add-on) for clear, simple visibility.


Information Security & Access Control
Secure access with multi-factor authentication and strict user authorization.
Stay Compliant. Manage IT with Confidence.
Built-In Security
Done Right
Location-Based Access Control
Set geofencing policies to block access from unauthorized regions keeping your data protected.

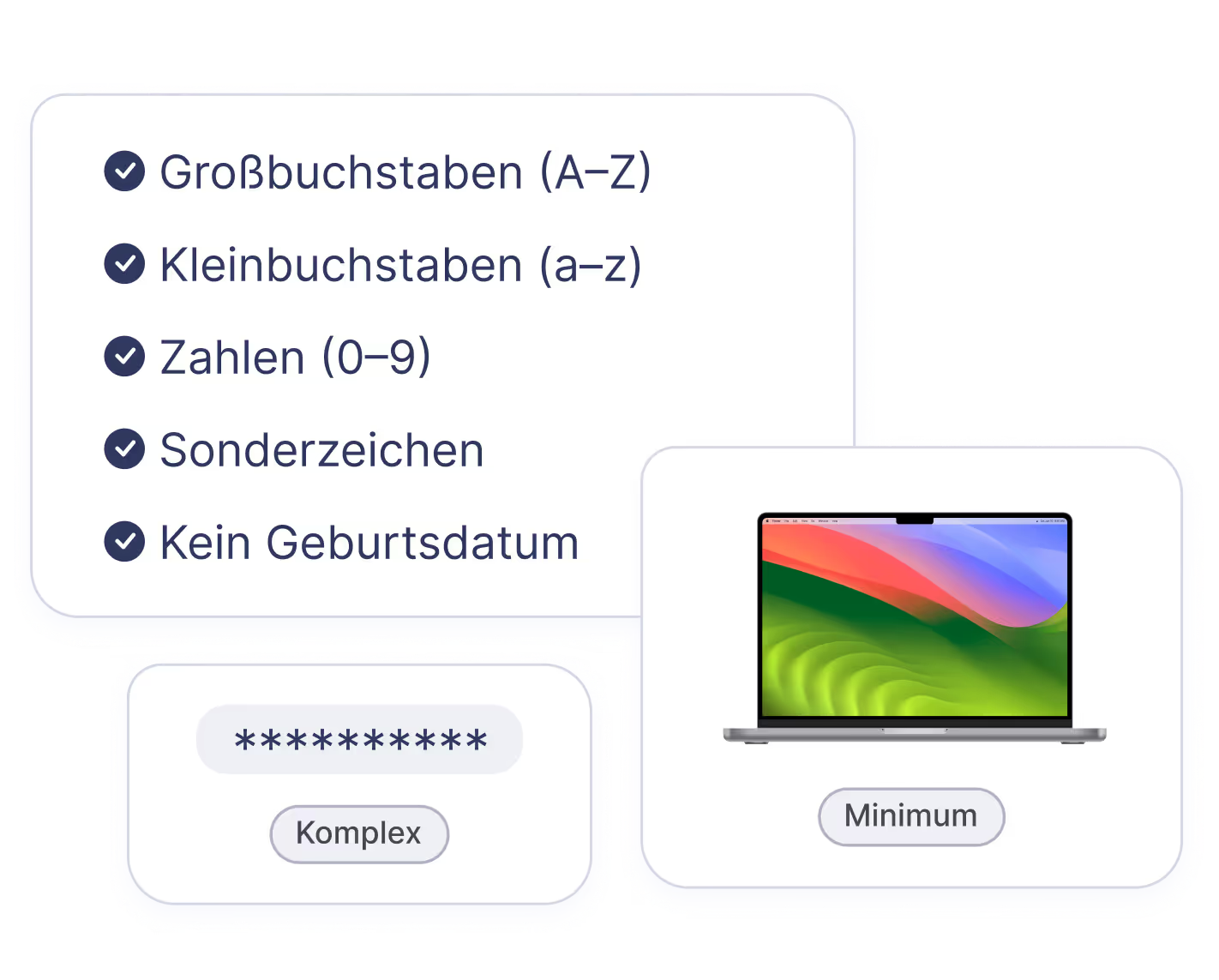
Encryption & Key Security
Devices use BitLocker or FileVault with secure key storage and verified access — ensuring strong data protection.

Asset & Device Management
Register devices, log access via digital lock systems, and maintain a clear overview of your hardware.

Complete Endpoint Protection: EPP + EDR
Stop known threats with EPP tools like antivirus & firewalls then add EDR for real-time monitoring, behavioral analysis, and automated response.










